Technology news, features and articles
Throughout history, the pursuit of technology to help us work harder, faster and more safely has led to some truly incredible inventions that have changed the world we live in — from the ancient tools first used by our ancestors to 21st-century breakthroughs such as bionic eyes and artificial intelligence (AI). Our expert writers and editors address the groundbreaking developments in robotics, quantum computing and much more with the latest future technology news, articles and features.
Latest about Technology
-
-
 Buying guides
Buying guidesBest sleep headphones 2025: From tiny earbuds and snuggly headbands to pillow speakers
By Anna Gora Last updated
-

New 'DNA cassette tape' can store up to 1.5 million times more data than a smartphone — and the data can last 20,000 years if frozen
By Fiona Jackson Published
-
 Buying guides
Buying guidesThe 22 best gifts for nature lovers and outdoor explorers, according to our experts
By Anna Gora Published
-

Breakthrough 3D wiring architecture enables 10,000-qubit quantum processors
By Tristan Greene Published
-

Scientists create new solid-state sodium-ion battery — they say it'll make EVs cheaper and safer
By Rory Bathgate Published
-

New 'physics shortcut' lets laptops tackle quantum problems once reserved for supercomputers and AI
By Owen Hughes Published
-

MIT invention uses ultrasound to shake drinking water out of the air, even in dry regions
By Owen Hughes Published
-
Explore Technology
Artificial Intelligence
-
-

When an AI algorithm is labeled 'female,' people are more likely to exploit it
By Damien Pine Published
-

Your AI-generated image of a cat riding a banana exists because of children clawing through the dirt for toxic elements. Is it really worth it?
By Akhil Bhardwaj Published
-

Experts divided over claim that Chinese hackers launched world-first AI-powered cyber attack — but that's not what they're really worried about
By Carly Page Published
-

Popular AI chatbots have an alarming encryption flaw — meaning hackers may have easily intercepted messages
By Peter Ray Allison Published
-

Switching off AI's ability to lie makes it more likely to claim it's conscious, eerie study finds
By Owen Hughes Published
-

The more that people use AI, the more likely they are to overestimate their own abilities
By Drew Turney Published
-

New 'Dragon Hatchling' AI architecture modeled after the human brain could be a key step toward AGI, researchers claim
By Owen Hughes Published
-

Some people love AI, others hate it. Here's why.
By Paul Jones Published
-

AI models refuse to shut themselves down when prompted — they might be developing a new 'survival drive,' study claims
By Ben Turner Published
-
Communications
-
-

Science history: First computer-to-computer message lays the foundation for the internet, but it crashes halfway through — Oct. 29, 1969
By Tia Ghose Published
-
 Science history
Science historyScience history: First two-way phone call across outdoor lines made by Alexander Graham Bell — Oct. 9, 1876
By Tia Ghose Published
-

Scientists invent 'Pulse-Fi' prototype — a Wi-Fi heart rate monitor that's cheaper to set up than the best wearable devices
By Sophie Berdugo Published
-

Scientists develop 'full-spectrum' 6G chip that could transfer data at 100 gigabits per second — 10,000 times faster than 5G
By Rich McEachran Published
-

Google has turned 2 billion smartphones into a global earthquake warning system — it's as effective as seismometers, tests show
By Ben Turner Published
-

Japan sets new internet speed record — it's 4 million times faster than average US broadband speeds
By Perri Thaler Published
-
Your data is being compromised much quicker than ever before, but you don't have to sit still and take it
By Mike Chapple Published
-

New 'super laser' amplifier could make the internet 10 times faster
By Peter Ray Allison Last updated
-

SpaceX's Starlink satellite constellation 'under threat' by Russia and China
By Sharmila Kuthunur Published
-
Computing
-
-

New 'DNA cassette tape' can store up to 1.5 million times more data than a smartphone — and the data can last 20,000 years if frozen
By Fiona Jackson Published
-

Breakthrough 3D wiring architecture enables 10,000-qubit quantum processors
By Tristan Greene Published
-

New 'physics shortcut' lets laptops tackle quantum problems once reserved for supercomputers and AI
By Owen Hughes Published
-
New semiconductor could allow classical and quantum computing on the same chip, thanks to superconductivity breakthrough
By Anna Demming Published
-

Scientists say they've eliminated a major AI bottleneck — now they can process calculations 'at the speed of light'
By Tristan Greene Published
-

Dream of quantum internet inches closer after breakthrough helps beam information over fiber-optic networks
By Owen Hughes Published
-

Quantum computing will make cryptography obsolete. But computer scientists are working to make them unhackable.
By Joanna Thompson Published
-

IBM unveils two new quantum processors — including one that offers a blueprint for fault-tolerant quantum computing by 2029
By Keumars Afifi-Sabet Published
-
Exotic 'time crystals' could be used as memory in quantum computers, promising research finds
By Anna Demming Published
-
Electric Vehicles
-
-

Scientists create new solid-state sodium-ion battery — they say it'll make EVs cheaper and safer
By Rory Bathgate Published
-

Watch four flying cars go toe-to-toe in new 'Formula One of the skies'
By Damien Pine Published
-

Toyota to launch world's first EV with a solid-state battery by 2027 — they're expected to last longer and charge faster
By Skyler Ware Published
-

New hydrogen battery can operate four times colder than before — meaning denser and longer-lasting EV batteries
By Roland Moore-Colyer Published
-

'Midnight' eVTOL smashes its own record in latest test flight — bringing us closer to operational flying taxis
By Alan Bradley Published
-

New EV battery tech could power 500-mile road trips on a 12-minute charge
By Owen Hughes Published
-

Meet the Chinese supercar that just smashed the EV speed record
By Sophie Berdugo Published
-

How 'flying boats' are bringing EVs to the ocean — with the help of LeBron James and Tom Brady
By Ben Turner Published
-
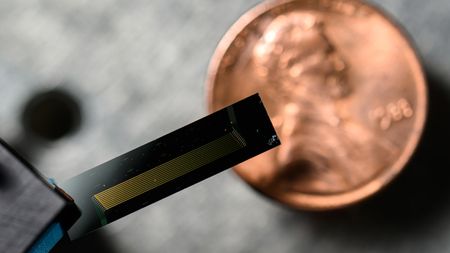
Penny-sized laser could help driverless cars see the world so much clearer
By Rory Bathgate Published
-
Electronics
-
-
 BUYING GUIDE
BUYING GUIDEBest astrophotography cameras 2025: Capture the Geminids
By Kimberley Lane Last updated
-
 BUYING GUIDE
BUYING GUIDEBest air purifiers 2025: Banish air pollution from your home
By Anna Gora Last updated
-

'Rainbow-on-a-chip' could help keep AI energy demands in check — and it was created by accident
By Owen Hughes Published
-

Self-healing 'concrete batteries' now 10 times better — they could one day power cities, scientists say
By Owen Hughes Published
-
 Buying Guide
Buying GuideBest laptops for photo editing 2025: Our top picks for working with images and videos on the move
By Keumars Afifi-Sabet Last updated
-
 Buying Guide
Buying GuideBest MacBooks for students 2025: Pick up a machine with immense performance in a portable frame
By Keumars Afifi-Sabet Last updated
-
 Buying Guide
Buying GuideBest electric toothbrushes 2025: For healthy teeth and a bright smile
By Joanne Lewsley Last updated
-
 Buying Guide
Buying GuideBest electric toothbrushes for kids 2025
By Joanne Lewsley Last updated
-

Electronics breakthrough means our devices may one day no longer emit waste heat, scientists say
By Tristan Greene Published
-
Engineering
-
-

MIT invention uses ultrasound to shake drinking water out of the air, even in dry regions
By Owen Hughes Published
-

NASA’s ultraquiet supersonic 'flying swordfish' makes history with first test flight
By Damien Pine Published
-

Science history: The Tacoma Narrows Bridge collapses, forcing a complete rethink in structural engineering — Nov. 7, 1940
By Tia Ghose Published
-

China's new 'solar-power window coating' can capture energy and power household devices
By Peter Ray Allison Published
-

A scalding hot 'sand battery' is now heating a small Finnish town
By Sophie Berdugo Published
-

Secretive X37-B space plane to test quantum navigation system — scientists hope it will one day replace GPS
By Samuel Lellouch Published
-

China builds record-breaking floating wind turbine — it could change the face of renewable energy
By Rory Bathgate Published
-

Could we ever build a transatlantic tunnel?
By Ashley Hamer Published
-

New York to Los Angeles in 3 hours? Executive order could make it possible by 2027, reopening the door for commercial supersonic flight
By Lisa D. Sparks Published
-
Internet
-
-
 Deals
DealsStream David Attenborough's Great Barrier Reef and many more nature documentaries with a 77% saving in this Paramount+ Black Friday deal
By Paul Brett Published
-
 Deals
DealsGet a host of brilliant science documentaries at your fingertips with Paramount Plus starting at just $2.99 a month
By Rich Owen Published
-

How to turn off web notifications for Google Chrome and macOS
By Jeanna Bryner Last updated
-
Follow Live Science on social media
By Livescience.com Published
-

Live Science daily newsletter: Get amazing science every day
By Livescience.com Published
-
 Reference
ReferenceInternet history timeline: ARPANET to the World Wide Web
By Kim Ann Zimmermann Published
-
 Reference
ReferenceTCP/IP: What are the rules of the internet?
By Laura Mears Published
-
 Reference
ReferenceLatency: Definition, measurement and testing
By Laura Mears Published
-
 Reference
ReferenceThe internet: History, evolution and how it works
By Laura Mears Published
-
Robotics
-
-
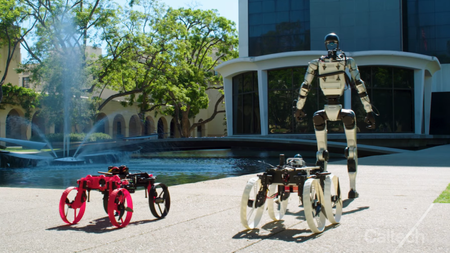
New 'Transformer' humanoid robot can launch a shapeshifting drone off its back — watch it in action
By Bobby Hellard Published
-

Bizarre robotic chair concept looks like a crab and can carry you around the house — it can even help you into your car
By Alan Bradley Published
-

Watch: Chinese company's new humanoid robot moves so smoothly, they had to cut it open to prove a person wasn't hiding inside
By Owen Hughes Published
-

Humanoid robots could lift 4,000 times their own weight thanks to breakthrough 'artificial muscle'
By Bobby Hellard Published
-

Scientists create ultrapowerful, squishy robotic 'eye' that focuses automatically and doesn't need a power source
By Stephanie Pappas Published
-

Watch new humanoid robot pirouette, pose and pull off deft karate moves with eerily lifelike movement
By Owen Hughes Published
-

Robots receive major intelligence boost thanks to Google DeepMind's 'thinking AI' — a pair of models that help machines understand the world
By Alan Bradley Published
-
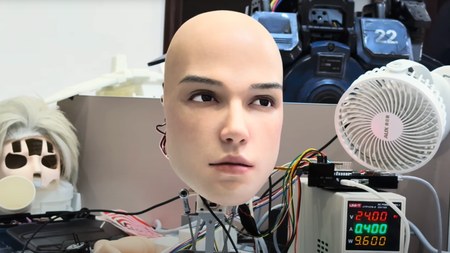
Chinese tech company develops creepy ultra-lifelike robot face — watch it blink, twitch and nod
By Skyler Ware Published
-

Scientists taught an AI-powered 'robot dog' how to play badminton against humans — and it's actually really good
By Sophie Berdugo Published
-
Virtual Reality
-
-

Watch people manipulate 3D holograms thanks to breakthrough technology
By Roland Moore-Colyer Published
-
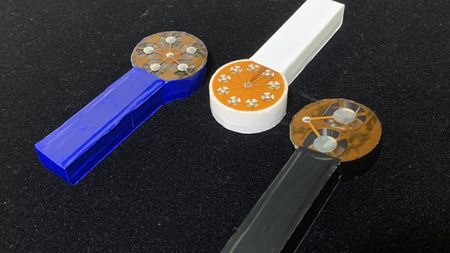
Weird lickable lollipop invention lets you taste in virtual reality
By Pandora Dewan Published
-

Future VR headsets could use a new type of lens inspired by holographic tech
By Andrea Saravia Pérez Published
-

AI-powered app performs full-body motion capture using just your smartphone — no suits, specialized cameras or equipment needed
By Keumars Afifi-Sabet Published
-

Playing with fire: How VR is being used to train the next generation of firefighters
By Ian Stokes Published
-

New display tech paves the way for 'most realistic' holograms in regular eyeglasses
By Drew Turney Published
-

Meta just stuck its AI somewhere you didn't expect it — a pair of Ray-Ban smart glasses
By Roland Moore-Colyer Published
-
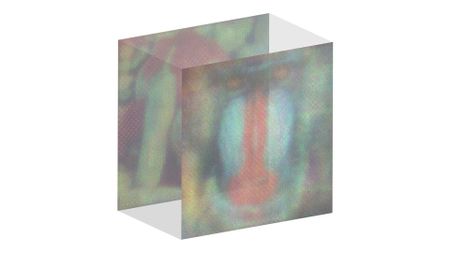
New invention transforms any smartphone or TV display into a holographic projector
By Owen Hughes Published
-

VR headsets vulnerable to 'Inception attacks' — where hackers can mess with your sense of reality and steal your data
By Drew Turney Published
-
More about Technology
-
-

MIT invention uses ultrasound to shake drinking water out of the air, even in dry regions
By Owen Hughes Published
-

When an AI algorithm is labeled 'female,' people are more likely to exploit it
By Damien Pine Published
-

Best spotting scopes in 2025 for birdwatching and wildlife observation
By Matt Morris Last updated
-

